Overview
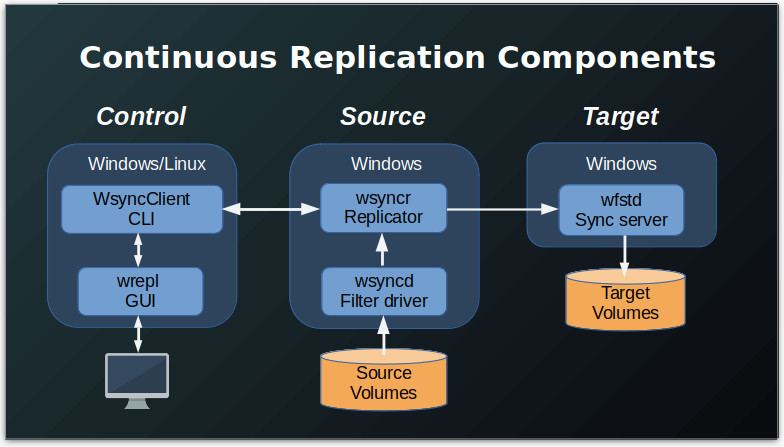
As shown in the figure below, the WANFast Continuous Replication runs on two or three machines:
- The Source machine -- the machine with the volumes that you want to replicate -- runs the wsyncd driver and the wsyncr replication process.
- The Target machine -- the machine with the volumes you want to receive the replicated data -- runs the wfstd server process.
- The Control machine -- the machine from which you will configure, monitor, and control the replication process -- runs the wsyncClient command line interface and wrepl graphical management program.
For the current release of WANFast Continuous Replication, the source and target machines must both be running Windows 2008R2 or later. The control machine can be any machine that is running either Windows or Linux and has network access to the source machine. You can also choose to install the control software on either the source or target machines, if this is easier. If you choose to do so, please perform all instructions described here for the control machine on whichever machine you installed the control software.
Preparing the Source Machine
The source machine is the machine that is being replicated. It will run the WANFast wsyncd driver in order to detect changes made to your volumes. Those changes will be read and accumulated by the wsyncr process, which will periodically send the changes to the wfstd process on the target machine. If running on a Windows computer, wsyncr will take a VSS snapshot of the volumes at the start of each interval so that it can access any locked files.
To prepare the source machine you will need to log into the source machine using an account with administrative access.
Install the Software
Run the WANFast Windows installer. Choose to install both the client side programs and the real-time volume replication. You do not need to select the WANFast service for incoming connections. For more detailed information on the installation process, see Install the Software.
Install the License File
For test purposes there is no need to install a license file. A 30-day trial license is created during installation. This is a full featured license.
For instructions on obtaining and installing a production license, see Install a Production License.
Preparing the Target Machine
The target machine is the machine to which the data will be replicated. It will run the wfstd process, which receives the sequence of changes from the source machine and writes them out to the target volumes according to your specifications. To prepare the target machine you will need to log into the target machine using an account with administrative access.
Install the Software
Run the WANFast Windows installer. Choose to install the client side programs and the WANFast service for incoming connections. Do not install the the real-time volume replication. For more detailed information on the installation process, see Install the Software.
Install the License File
For test purposes there is no need to install a license file. A 30-day trial license is created during installation. This is a full featured license.
For instructions on obtaining and installing a production license, see Install a Production License.
Preparing the Control Machine
The control machine runs the wsyncClient command line program and the wrepl graphical user interface. These are used to configure, manage, and monitor the replication process. The control software can be installed on any Windows or Linux machine that has network access to the source machine. You can install the control software on as many machines as you like, but there is a limit of four concurrent connections to the wsyncr process.
Log into the control machine using an account with administrative access. Note that this is not necessary to run the control software on the source or target machines as it has already been installed there.
Install the Software
Run the WANFast Windows installer. Choose to install the client side programs. You do not need to install the real-time volume replication or the WANFast service for incoming connections. For more detailed information on the installation process, see Install the Software.
Install the License File
You do not need a WANFast license in order to run the replication control software.
Configuring Secure Access
To ensure the security of your data, the WANFast software requires strict Identification and Authorization for all activity. It will use strong encryption (optionally up to NIST standards AES-256 and SHA-256) to ensure the privacy and integrity of all communications and data. See WANFast Security for more details.
Create a Key Pair for Each Administrative User
Each user that will administer the replication process will need to create a WANFast key pair on the control machine that they will use for administrative access. They will need to log into the control machine using their personal account -- no need for administrative access. They should follow the instructions for Creating a WANFast Key Pair.
Authorize Each Administrative User
A user must be explicitly authorized to access the wsyncr application running on the source machine. A user becomes authorized when an Administrator of the source machine adds the user's public key (C:\Users\AccountName\AppData\Local\WANFast\wfst.pub located on the control machine) to the source machine's authorization file, C:\ProgramData\WANFast\authorized_keys. Note that each key must take up exactly one line in the authorization file. If you use cut and paste to add the public key to the authorization file, be sure that it doesn't add carriage returns, new lines, or spaces to the file. It is generally safer to use the command:
type C:\PathToPublicKey\wfst.pub >> C:\ProgramData\WANFast\authorized_keys
to append USER's public key file to the end of the authorization file. Be sure to run the command:
wfstPerms -s
afterwards to make sure that you haven't changed the file permissions. Leaving the authorization file with incorrect permissions might compromise the security of your data as another user might be able to add their key to the file and access the data on your computer.
Authorize the Source Machine for Replication to the Target
In order to replicate data from the source machine to the target machine, the source must be authorized for access to the target. The source becomes authorized when an Administrator of the target machine adds the source machine's public key (C:\ProgramData\WANFast\wfst.pub on the source machine) to the target machine's authorization file, C:\ProgramData\WANFast\authorized_keys. See the comments above on how to copy a public key into the authorization file. Be sure to run wfstPerms -s when finished.
Replicating Multiple Source Machines to a Single Target Machine
A single target machine can serve as the replication target for any number of source machines. There are some simple rules to ensure the consistency of your data:
- Be sure to map each source to a separate location within the target's storage. For example:
- You can migrate each volume on the many source machines to a separate volume on the target machine.
- Or you can migrate each source machine to a separate volume on the target machine. Put each source volume into a different subdirectory on the target volume.
- Or you can migrate multiple sources to a single target volume by targeting each to a separate subdirectory on the target volume.
- If the target is to be used for Disaster Recovery, you will probably want to run with the --consistent-target option. This uses VSS snapshots on the target to ensure that either all or none of a data set gets updated to the target. This guarantees that the target disks are always in an internally consistent state. To support target consistency each source machine must be replicated to a different set of target volumes. You can still consolidate multiple source volumes to a single target volume, but be sure that only a single source machine is replicating to any one volume on the target.
The Configuration Files
The wrepl configuration is stored in the wsyncr.gui file in your WANFast directory on the control machine. It is primarily used to save your connection information to the source machine.
On the source machine the file C:\ProgramData\WANFast\wsyncr.cfg stores:
- the configuration for the wsyncr process,
- the source machine's connection information for the target machine,
- the volume mapping between the source and the target machines,
- and the initial state and configuration of the continuous replication process.
After you have configured the process using wrepl and saved the configuration, the source machine can be shutdown and restarted and the replication process will restart automatically.